The $90 million hack of Iran’s largest crypto exchange, Nobitex, made global headlines. But newly surfaced blockchain data shows the breach exposed something bigger.
A forensic report by blockchain intelligence firm Global Ledger found that months before the June 18 attack, Nobitex was systematically moving user funds using techniques commonly associated with money laundering.
Was Iran’s Nobitex Exchange Laundering User Funds Before the Hack?
On-chain data shows that Nobitex employed a method called peelchaining. This is when large amounts of Bitcoin are split into smaller chunks and routed through short-lived wallets.
The technique makes fund tracing difficult and is often used to obscure the origins of money. In Nobitex’s case, analysts found a pattern of BTC being cycled in consistent 30-coin chunks.
Global Ledger also found that Nobitex used temporary deposit and withdrawal addresses—a behavior known as chip-off transactions. These one-use addresses funnel BTC into new wallets, disguising liquidity trails.
The “Rescue Wallet” Wasn’t New
After the hack, Nobitex claimed it moved remaining funds as a safety measure. On-chain activity did show a 1,801 BTC sweep (worth ~$187.5 million) into a newly created wallet.
But this wallet wasn’t new. Blockchain data traces its historical use back to October 2024. The wallet had long been collecting chipped-off funds.
This “rescue wallet” received multiple 20–30 BTC transfers that followed the same laundering-like patterns, even before the hack occurred.
Post-Hack Activity Shows Continued Control
Hours after the breach, Nobitex moved funds from its exposed hot wallet to another internal address. This full-balance sweep indicated Nobitex retained operational control.
On June 19, investigators observed 1,783 BTC transferred again to a new destination wallet. This matched Nobitex’s public claim of securing its assets—but now with added context.
The flows suggest that rather than reacting to the hack, Nobitex was simply following its pre-existing money laundering playbook.
The pro-Israel hacking group Gonjeshke Darande published files exposing Nobitex’s internal wallet structure.
The hack may have shocked users, but blockchain data shows that Nobitex had already been moving funds this way for months.
Old wallets linked to the exchange were regularly sending Bitcoin to new wallets. From there, the funds were broken into smaller amounts and moved again and again—often in chunks of 20 or 30 BTC.
This method makes it harder to track where the money ends up. It’s similar to how some people hide their tracks when moving funds through crypto.
What’s important is that this wasn’t something Nobitex started after the hack. They had been doing it long before, and they kept doing it after—almost like it was standard procedure.
One wallet in particular—bc1q…rrzq—shows up again and again. It received lots of user deposits and appears to be the starting point for many of these hard-to-trace fund movements.
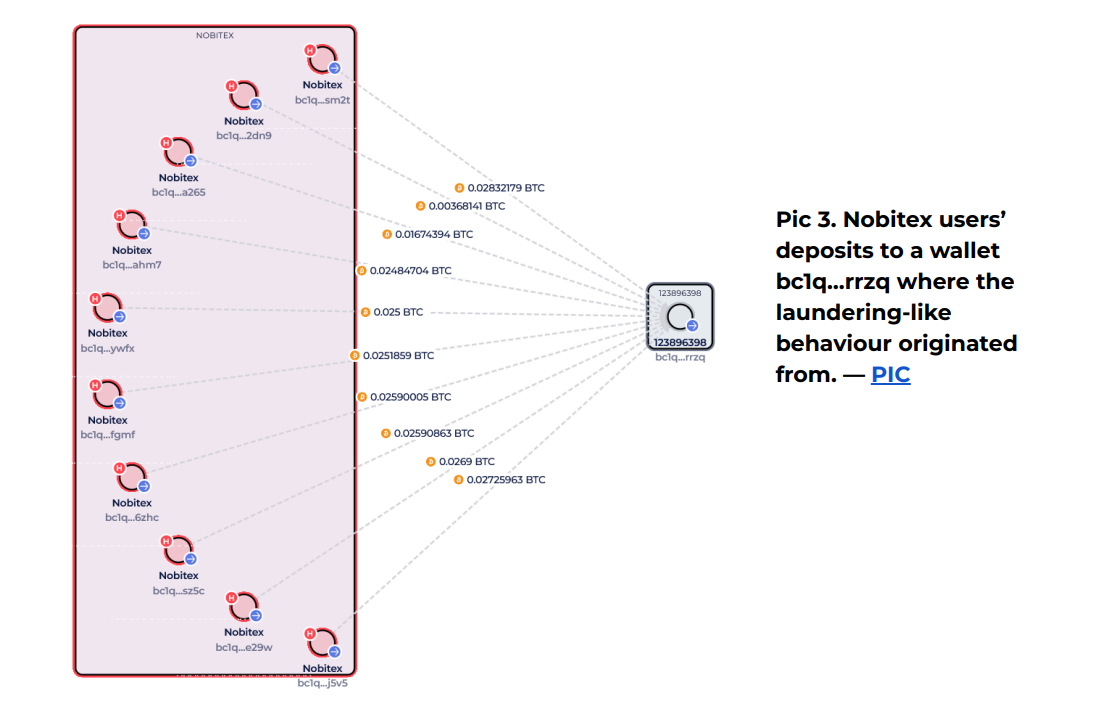
In short, the hack didn’t cause Nobitex to change how it handled funds. It simply brought ongoing behind-the-scenes activity into the public eye.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.
Read the full article here