Web3 security experts consider North Korea’s Lazarus Group the most prominent and sophisticated threat to the crypto industry in 2024.
Earlier this week, the infamous Lazarus Group reportedly funneled $12 million through crypto tumbler Tornado Cash. The funds were allegedly linked to last November’s HTX and Heco Bridge hack, which saw the platforms lose over $90 million.
However, this wasn’t the group’s only heist in 2023. Throughout the year, the North Korea-backed hackers compromised over $400 million worth of assets across various crypto platforms, including CoinEX, Poloniex, Stake.com, and Atomic Wallet. In 2022, the group was responsible for the biggest defi hack in history, as it compromised the Ronin Network to steal approximately $620 million.
Lazarus’s hacks occurred during a prolonged bear market in the crypto industry, reeling from the effects of FTX and Terra Luna’s collapse. In 2024, with the bull market running in full swing, significant tokens reaching all-time highs, and novel meme coins driving billions of dollars inflow into the market, Lazarus’s concerns are more prominent than ever.
Lazarus hacks in the second half of 2023
You might also like: FOMO and panic buying cost meme coin traders millions
To understand how the industry should prepare for such risks, crypto.news reached out to web3 security provider Cyvers, which exclusively detected the Poloniex hack last year.
How does Lazarus carry out its million-dollar crypto heists?
According to Cyvers CEO Deddy Lavid, the Lazarus Group has shifted its cyberattack strategies significantly in 2023, targeting centralized entities with a refined and dynamic approach. Moving beyond traditional phishing and brute force methods, the group now employs AI-driven phishing campaigns and complex smart contract exploits.
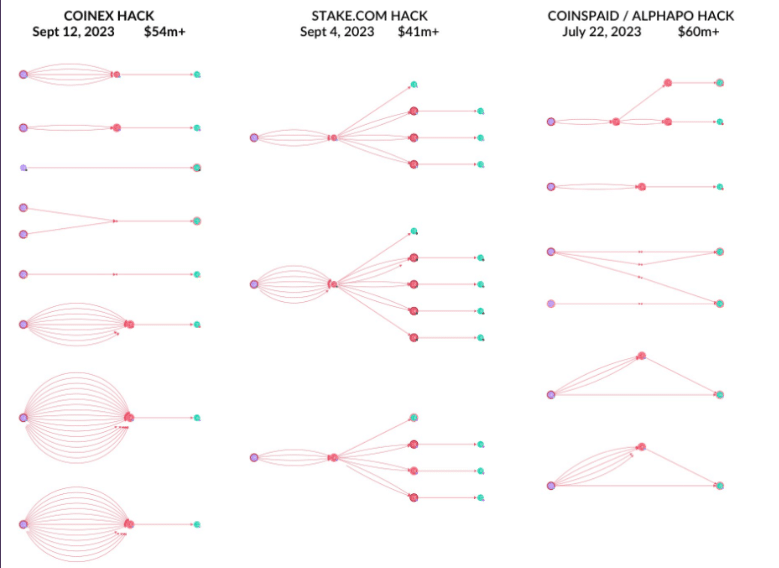
Onchain Topologies used by Lazarus hackers | Image provided by Cyvers
Specifically, the attacks on Poloniex and HTX focused on stealing private keys and launching a series of small attacks in a short period. The group also used pre-programmed bots to run automated attacks. The bots tend to live in a system for a long time undetected before starting to exfiltrate the assets.
Lavid also mentioned that Lazarus Group’s operational methods resemble military precision, reflecting a rare level of professionalism among cybercriminal syndicates. Lavid outlines a recurring pattern in their attacks: initial infiltration through social engineering, remaining dormant within the target organization for months, and stealing private keys for a series of quick, well-orchestrated attacks involving dry runs and fast, anomalous transaction rates.
The preparatory phase is followed by dispersing the stolen assets across multiple blockchains, eventually funneling them through mixers or exchanges for laundering.
So, while the crypto bull run of 2024 offers an exhilarating prospect for investors and innovators alike, it also presents an urgent call to arms for the security sector.
“My analysis emphasizes the need for increased security measures in the cryptocurrency and blockchain space, urging a deeper recognition of information security’s importance, a call for more security professionals, and a focus on proactive attack prevention.”
– Deddy Lavid, CEO at Cyvers
In 2024, Lavid foresees a crypto market that outgrows its nascent vulnerabilities to adopt a more mature approach to security.
Crypto platforms need to allocate greater resources towards developing security expertise within companies and a holistic strategy that preempts attacks and comprehensively addresses potential fraud across the blockchain.
Read more: British citizen found guilty in $6b Bitcoin fraud scheme
Read the full article here

